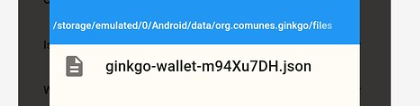
Does your file manager have access to others directory?
Mon gestionnaire de fichier me permet de naviguer sur tous les répertoires. J’ai même activé l’affichage des fichiers caché.
Mais je ne trouve pas le répertoire utilisé par l’application.
Je suis un utilisateur basique, Mes compétences sont très basses. Mais je pense que cette application est prévue pour les utilisateurs comme moi.
My file manager allows me to browse all directories. I have even activated the display of hidden files.
But I can’t find the directory used by the application.
I am a basic user, my skills are very low. But I think this application is meant for users like me.