Post écrit en anglais comme je ne sais pas trop quel développeur parle quelle langue (n’hésitez pas à répondre en français si vous préférez ![]() )
)
I made a proof of concept merge request for GCli which adds (sqlite) db persistence for the vault keys of the different SecretFormat types (Seed, Substrate, Cesium, (Predefined)) and also supports derivations for all of those.
Small reminder, I’m still new to the rust language so don’t hesitate to give constructive remarks ![]()
In more details:
DB persistence
I picked up crate sea-orm (first time using db with rust so there might be a better dependency - but I wanted support for entity mapping without having to manually create the tables).
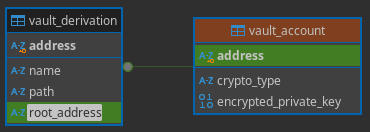
DB Tables:
vault_account
One vault_account is created per root key and it contains the encrypted substrate uri for that key.
Examples (you can find source of those cases in the derivations tests I added):
crypto_type: Sr25519Mnemonic
encrypted_private_key(decrypted): "bottom drive obey lake curtain smoke basket hold race lonely fit walk"
crypto_type: Sr25519Seed
encrypted_private_key(decrypted): "0xf813535799c3a15b8e419a06964e87fabd3f265caebcbb38c935a1acdbe05253"
crypto_type: Ed25519Seed
encrypted_private_key(decrypted): "0x2101d2bc68de9ad149c06293bfe489c8608de576c88927aa5439a81be17aae84"
This substrate uri format allows to easily compose the derivation by just adding the derivation path after it. In thoses cases here, I believe the seed is also called mini-secret.
fields:
addressString: The SS58 Address of the root keycrypto_typeString: “Sr25519Mnemonic” / “Sr25519Seed” / “Ed25519Seed”- The
Ed25519Seedis used for Cesium V1 keys; see it’s derivation test
Maybe using this kind of Ed25519 seed constructed usingnacl::sign::Keypairwhich we construct with cesium v1idandsecretis not a good idea for security reasons
- The
encrypted_private_keybytes: encrypted substrate uri using the same encryption that was used for the vault files (might need to be adapted )
)
vault_derivation
For each of those (root) vault_account one vault_derivation is created with path at None and both address and root_address having the same value.
Then to add a derivation, we only need one extra row in vault_derivation that have a valid non-null path value and refers to the correct root_address
fields:
addressString: The SS58 Address of this specific derivation (ifpathis None, then it’s the root address)nameOption<String>: allows to have a vault name associated with any of the vault key derivation; it has a unique constraint to avoid issuespathOption<String>: allows to provide the derivation path which should beNoneor a string starting with'/'root_addressString: The SS58 Address of the root for this derivation. It is also a foreign key to thevault_accounttable.
Adapted/Extra vault commands
I added dialoguer updated inquire crate dependency because of a bug for the password confirmation in the version 0.6.2 we were using.
Using it to manage extra input (see in inputs.rs)
(We might want to also convert remaining usages of rpassword crate and remove that dependency ![]() )
)
list [all|root] command
I adapted the list command into 2 sub commands.
gcli vault list --help
List available keys
Usage: gcli vault list <COMMAND>
Commands:
all List all keys and derivations in the vault
root List only root keys
help Print this message or the help of the given subcommand(s)
Options:
-h, --help Print help
list all: that will list all the keys and their derivations in order; also computing a derivation name if it doesn’t have a name but it’s root key does.
Values inside ‘<…>’ are computed.
example output:
gcli vault list all
available keys:
┌──────────────────────────────────────────────────────────────────────────────────────────┐
│ SS58 Address Path Vault Name │
╞══════════════════════════════════════════════════════════════════════════════════════════╡
│ 5DfhGyQdFobKM8NsWvEeAKk5EQQgYe9AydgJ7rMB6E1EqRzV <Root> mySubstrateKey │
│ 5D34dL5prEUaGNQtPPZ3yN5Y6BnkfXunKXXz6fo7ZJbLwRRH //0 <mySubstrateKey//0> │
│ 5GBNeWRhZc2jXu7D55rBimKYDk8PGk8itRYFTPfC8RJLKG5o //1 substrateDeriv1CustomName │
│ 5GrwvaEF5zXb26Fz9rcQpDWS57CtERHpNehXCPcNoHGKutQY //Alice <mySubstrateKey//Alice> │
│ 5ET2jhgJFoNQUpgfdSkdwftK8DKWdqZ1FKm5GKWdPfMWhPr4 <Root> myCesiumKey │
│ 5Ca1HrNxQ4hiekd92Z99fzhfdSAqPy2rUkLBmwLsgLCjeSQf //0 <myCesiumKey//0> │
│ 5GjAp6kkbsDjxABGouMvu1Mxbr7PaFqbMrprEoZ466vPF2Vt <Root> mySeedKey │
│ 5HBwy19piXNWg7bfShuNgWsBCWRzkG99M8eRGB6PHkxeAKAV //0 <mySeedKey//0> │
└──────────────────────────────────────────────────────────────────────────────────────────┘
list root: only shows root keys for easier selections for the derivation command
example:
gcli vault list root
available root keys:
┌────────────────────────────────────────────────────────────────────────────┐
│ SS58 Address Path Vault Name │
╞════════════════════════════════════════════════════════════════════════════╡
│ 5DfhGyQdFobKM8NsWvEeAKk5EQQgYe9AydgJ7rMB6E1EqRzV <Root> mySubstrateKey │
│ 5ET2jhgJFoNQUpgfdSkdwftK8DKWdqZ1FKm5GKWdPfMWhPr4 <Root> myCesiumKey │
│ 5GjAp6kkbsDjxABGouMvu1Mxbr7PaFqbMrprEoZ466vPF2Vt <Root> mySeedKey │
└────────────────────────────────────────────────────────────────────────────┘
Setting / Using vault name
I adapted the base argument -a <ADDRESS> to support one of -a <ADDRESS> or -v <NAME>.
-v <NAME>: Vault name for a key
This same choice of Address / VaultName is also allowed for several of the vault commands
A computed VaultName can be provided as well (example mySubstrateKey//Alice from the list above)
This VaultName can be set when importing a key, or with new vault rename command.
use command
gcli vault use --help
Use specific vault key (changes the config address)
Usage: gcli vault use <-a <ADDRESS>|-v <NAME>>
Options:
-a <ADDRESS> key SS58 Address
-v <NAME> Vault name for a key
-h, --help Print help
import command
Adapted to allow providing the Secret key format but still takes substrate as default if not provided
gcli vault import --help
Import key from (substrate)mnemonic or other format with interactive prompt
Usage: gcli vault import [OPTIONS]
Options:
-S, --secret-format <SECRET_FORMAT> Secret key format (substrate, seed, cesium) [default: substrate]
-h, --help Print help
derivation command
gcli vault derivation --help
Add a derivation to an existing (root) vault key
Usage: gcli vault derivation <-a <ADDRESS>|-v <NAME>>
Options:
-a <ADDRESS> key SS58 Address
-v <NAME> Vault name for a key
-h, --help Print help
also has aliases deriv and derive
rename command
gcli vault rename --help
Give a meaningful vault name to a vault key or derivation
Usage: gcli vault rename <ADDRESS>
Arguments:
<ADDRESS> key SS58 Address
Options:
-h, --help Print help
remove command
gcli vault remove --help
Remove a vault key (and potential derivations if it's a root key)
Usage: gcli vault remove <-a <ADDRESS>|-v <NAME>>
Options:
-a <ADDRESS> key SS58 Address
-v <NAME> Vault name for a key
-h, --help Print help
list-files command
gcli vault list-files --help
(deprecated)List available key files (needs to be migrated with command "vault migrate" in order to use them)
Usage: gcli vault list-files
Options:
-h, --help Print help
migrate command
gcli vault migrate --help
(deprecated)Migrate old key files into db (will have to provide password for each key)
Usage: gcli vault migrate
Options:
-h, --help Print help